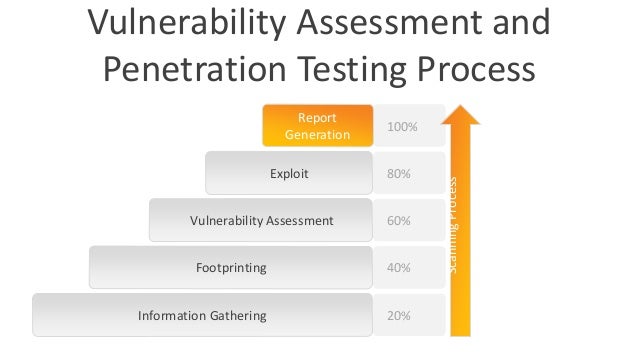
Penetration Testing Steps
Metasploit is the world’s most used penetration testing software. Uncover weaknesses in your defenses, focus on the right risks, and improve security.
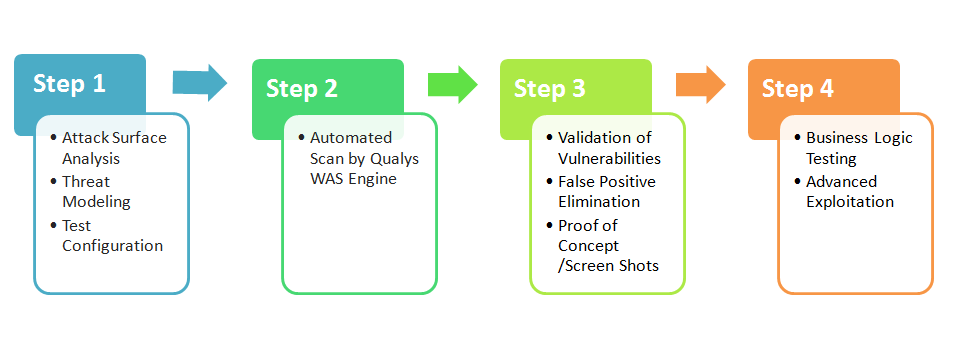
HackLabs is a Security Consulting Company specialising in Penetration Testing, Ethical Hacking, Web Application Security, using thorough and appropriate testing …
Penetration Testing. Here at Corsaire we can help you with everything you need to know about Penetration Testing. Our advanced penetration tests are a fundamental part of your organisational risk-management process, whereby we examine the resilience of your security to identify vulnerabilities and weaknesses in systems such as networks
Learn penetration testing strategies, ethical hacking techniques to help security professionals evaluate the effectiveness of information security …
Wireless Penetration Testing Checklist Wireless Penetration testing is the Actively Examine the Process of Information security Measures which is Placed
The Advanced Penetration Testing Course by EC-Council was created as the progression after the ECSA (Practical) to prepare those that want to challenge the Licensed Penetration Tester (Master) certification and be recognized as elite penetration testing professionals.

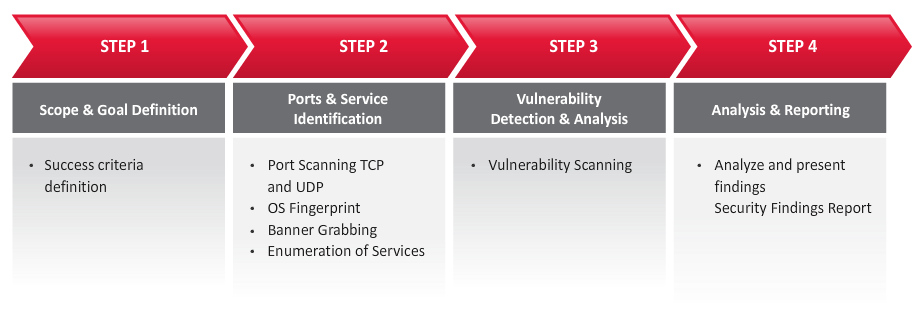
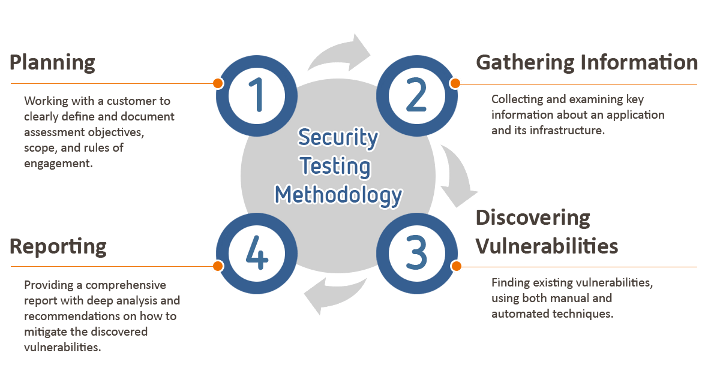


HackLabs’ Internal Penetration Test follows documented security testing methodologies to find weaknesses in network security and …

This network penetration testing guide reveals how to use penetration testing tools and best practices for conducting a penetration test.
Penetration Testing Professional (PTP) is the premier online penetration testing course that teaches all the skills needed to be a professional penetration tester, including report writing and hands-on labs.
The only way to know your systems are secure is to test them. Learn how to use penetration testing to check for vulnerabilities in computers, networks, applications, email, and people.